ThinScale Management Console Admin Guide - Access Keys
This article will describe the access keys of the Management Console.
ACCESS KEYS
Access Keys are the entry point for all devices into the Management Platform. You can create any number of Access Keys that different devices can connect. For example, you can create two Access Keys with different credentials and device folders. This will allow different devices connecting via the different Access Keys to require different credentials and can be registered into different device folders in the console, assigning different profiles and packages if desired.
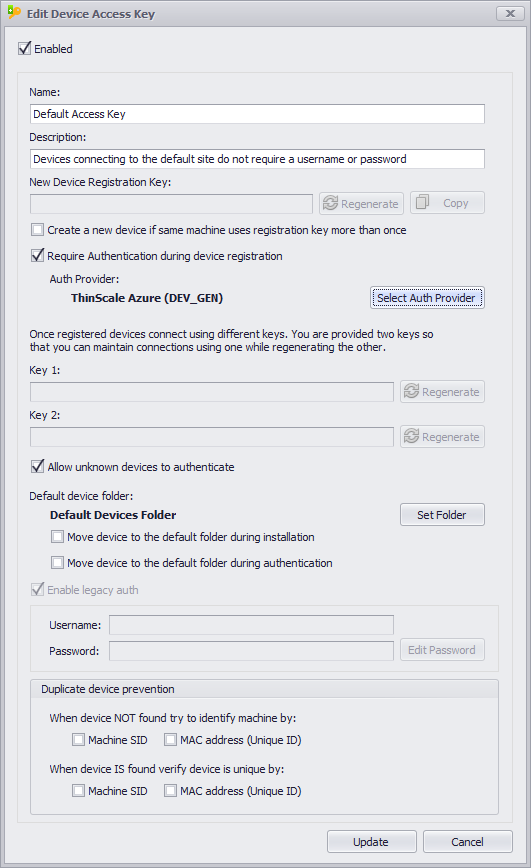
- Enter a Name and Description for your new Access Key.
- Access Keys have three keys associated with them.
- Device Registration Key – Used by devices during initial installation.
- Key1 and Key2 – Used by devices to connect after installation. - Changing the Device Registration Key will not impact existing devices, but new installations must provide the updated key during installation.
- Create a new device option – if enabled every time a machine re-uses the registration key, a duplicate entry is created in the Management Console.
- Require Authentication – if enabled during installation the machine will be forced to authenticate against an Authentication Provider (i.e., Azure, Okta or LDAP if the domain is available).
- Devices can use either Key1 or Key2 to authenticate to the Management Server. As long as one key is correct, the device will authenticate.
- Using two keys allows the keys to be rotated without having to reinstall or reconfigure the devices using them.
- Change the default device folder so new devices are placed into that folder. This way, the new device will automatically adopt the required Profile and Software Packages on login.
ENABLE LEGACY AUTH
Legacy authentication allows older devices (pre-V7) to connect to the Management Server. Legacy authentication uses the same username and password authentication as the older Sites feature.
During the upgrade of your Management Server, all existing Sites will have an Access Key created with legacy authentication enabled and will use the same site username and password, meaning there will be no interruption to your existing devices.
When deploying ThinKiosk or Secure Remote Worker V7, we recommend using Access Key authentication instead of legacy authentication.